The intricacies of geo-blocking stem from its
ever-changing landscape, characterized by daily updates to subnet allocations
for each country and its businesses. Furthermore, generalized statements like
"block North Korea" are largely ineffective. To block a specific
nation or business network space accurately, one must recognize that the
targeted entities may have allies or alternate locations capable of hosting
attacks or communication servers.
It is essential to note that adept attackers
rarely launch assaults from their personal, corporate, or domestic IP
addresses. Most attacks can be inexpensively hosted on various cloud platforms
across numerous countries.
The rapid growth of cloud services, such as
Amazon, Azure, Google, and smaller providers, has created a borderless internet
that transcends national boundaries. As a result, an attacker's physical
location, including their country of origin, becomes less relevant than the
network space (business) they are operating within. The availability of hosting
providers enables attackers to shift their locations between countries
effortlessly, further complicating pinpointing their exact whereabouts.
Despite the widespread integration of security
measures like firewalls with geo-filtering capabilities, there has been a
noticeable stagnation in innovation within this domain over the past 15 years.
The predominant methods employed tend to utilize generalized strategies, often
insufficient in achieving their desired outcomes.
Palo Alto NG firewalls offer various
solutions, each boasting unique strengths. In this discussion, we will focus on
one particular feature, Country Blocking, to illustrate the differences between
basic country blocking found within firewalls and more sophisticated
geo-targeting capabilities.
Geo-targeting and geo-blocking are unique
concepts that require a clear understanding of inbound and outbound traffic to
appreciate their intricacies fully. While most firewall systems can effectively
identify users, ports, and applications for outbound traffic, they are
restricted to countries and ports when handling inbound traffic.
Geo-targeting, commonly associated with
marketing and content delivery, can also play a crucial role in network defense
and security. By leveraging the geographic location of businesses, deceptive
assets, Security Rule Orchestrator, and networks, administrators can implement
tailored security measures and proactively protect their digital assets from
potential threats from specific regions. In network defense and security,
geo-targeting offers the following benefits:
Enhanced Threat Detection:
Geo-targeting
enables security systems to monitor and analyze traffic patterns based on
users' geographic locations, including the businesses within those
geolocations. Network administrators can prioritize threat detection and
mitigation efforts by focusing on high-risk businesses, regions, and
countries known for cyber threats, leading to more efficient use of
resources.
Regional Access Control:
Network
administrators can create customized access control policies for different
regions and businesses by geo-targeting. This approach allows
organizations to restrict or grant access to their network resources based
on the user's country location and the business network they are operating
from, thereby minimizing the risk of unauthorized access and potential
data breaches.
Incident Response Management:
Geo-targeting
can inform incident response strategies by identifying the geographic
origins of cyberattacks at the business level. This information helps
security teams better understand threat actors' tactics, techniques, and
procedures (TTPs) and develop more effective countermeasures tailored to
specific regions.
Regulatory Compliance:
In some
industries, organizations must adhere to data protection regulations
restricting data access or transfer to specific countries. Geo-targeting
helps organizations comply with such regulations by ensuring that
sensitive information is only accessible to authorized users in designated
locations.
Proactive Defense:
Geo-targeting
can be used to implement proactive defense measures, such as blocking
traffic from countries and businesses with a high prevalence of cyber
threats or setting up honeypots in targeted locations. This proactive
approach helps organizations avoid potential threats and reduce their
attack surface.
For instance, a firewall can restrict
connections from specific user groups to designated countries, ports, or
applications. In comparison, inbound country filtering understandably needs
such user control. The primary objective is to secure the system by preventing
unauthorized connections from accessing or reaching undesirable locations.
To fully grasp the potential of geo-targeting,
it's crucial to understand the wide-ranging benefits of granular geo-targeting:
Enhanced
Intelligence: Geo-targeting systems leverage geographic data to pinpoint
and blacklist sources originating from specific regions.
Fine-Grained
Business Filtering: Geo-targeting delves into individual countries and
their respective businesses, enabling the application of tailored policies
at a more detailed level.
Adaptive
Defense Mechanisms: Geo-targeting is linked to dynamic response systems
that vary and adapt based on the source's target. These targets are
evaluated according to factors such as country, business, rate, and time.
Streamlined
Vendor Risk Management: By taking business locations into account,
geo-targeting assists in managing vendor risks more effectively. This
enables customers to accurately monitor vendor activity within their
environment.
Contextualization:
Examining telemetry at the business level sheds light on both the country
and the businesses operating within it. This approach leads to a more
robust policy design with fewer gaps and tighter controls.
Performance
Optimization: Traditional firewalls may require additional rule exceptions
to counteract the effects of broad-stroke filtering when blocking an
entire country. Granular geo-targeting offers a more efficient way to
accommodate country-specific nuances without requiring large and complex
rule sets.
Geo-blocking is often pigeonholed as a
one-dimensional solution primarily employed to " block a country."
Yet, this relatively simple security measure possesses an untapped potential
for a more diverse and lean-forward security strategy. When implemented
effectively, geo-blocking becomes geo-targeting and is a formidable
impenetrable defense against attackers, particularly when integrated with
Contextualization, Moving Target Defense, Business Intelligence, and Deceptive
Assets.
Let's take a moment to examine the evolution
of the Country Blocking feature.
If you would compare your firewall
geo-blocking feature today and the same feature five years ago, you will find
the feature has essentially been frozen in time, despite possible improvements
to specific underlying capabilities.
The thrust of their firewall's geo-blocking
technology is to provide an organized list of networks that have been assigned
through
IANA and update those lists periodically,
then they can be used to apply rules. Many years ago this was a good tool, but
lately, its turned into a very narrow use case and widely accepted that basic
geo-blocking is too broad and often ineffective. PacketViper, on the other
hand, has long understood that a more comprehensive approach to geo-targeting
is necessary for today's interconnected global landscape. As early as 2011, we
recognized this need and developed granular geo-targeting capabilities beyond
simple country blocking.
In this article, we will demonstrate
PacketViper's geo-targeting capabilities with any NG-Firewall geo-blocking
feature to offer a clear perspective on their respective capabilities. While
some customers may believe that country blocking alone provides sufficient
security, it is important to understand that it is just one small aspect of
geo-targeting. Users may be lulled into a false sense of security by relying
solely on the country blocking, as this approach often needs to be revised in
blocking specific threats. It is, therefore, crucial to adopt a more
comprehensive approach to geo-targeting, such as PacketViper's solution.
PacketViper revolutionized the field of
geo-targeting by introducing a granular system that not only restricts
connections but also enhances firewall performance, gathers and applies
intelligence, and reduces logging by almost 60%. Our innovative technology has
been so successful that we have received patents and built other solutions
around our core geo-targeting technology.
Our expertise in granular geo-targeting has
enabled us to offer cutting-edge technologies such as Moving Target
Defense/Deception, Dashboards, Decoy Responders, and Behavior Sensors,
capabilities that traditional firewalls cannot match.
Proper geo-targeting with granular
capabilities provides a more robust defense by confusing attackers, closing the
proxy loophole, and delivering more accurate intelligence than any firewall
feed currently available. With PacketViper's solution, you can achieve a level
of protection and sophistication unmatched by any other geo-targeting system.
Our solution is designed with ease of use,
enabling customers to examine and filter any geo-targets down to the business
level within a country with just a few clicks on our context-driven dashboard.
In contrast, geo-blockers used by platforms like Palo Alto and other firewalls
often punish entire countries and their businesses. At PacketViper, we
understand that, in most cases, it is not the entire country that poses a
threat but rather rogue business elements within them.
PacketViper's granular geo-targeting approach
to security when compared to other firewall solutions, such as those provided
by Palo Alto Networks, Fortinet, and Cisco. These platforms often rely heavily
on collective intelligence, which can limit customers' control over their
security infrastructure.
PacketViper differentiates itself by offering
a granular geo-targeting approach that empowers customers through features like
Moving Target Defense, Behavior Sensors, Vendor Management, Decoy Responders,
and Sirens. Each of these features can be tailored to meet specific customer
requirements. This allows for a more personalized security strategy, as opposed
to the shared protective measures distributed to millions of users by other
firewall manufacturers.
Many next-generation (NG) firewalls, including
those from leading providers, employ intrusion detection and prevention systems
(IDS/IPS) based on pre-established and known threat vectors. PacketViper, on
the other hand, is not constrained by these limitations. Our solution adopts a
unique approach to behavior and geo-targeting, utilizing deceptive assets
within the security context. This innovation enables a more comprehensive and
adaptable security framework, providing an added layer of protection for our customers.
Importance of a Layered Defense
Strategy for Enhanced Cybersecurity
A robust cybersecurity strategy necessitates
the implementation of a layered defense approach, wherein each layer comprises
the best possible security measures tailored to specific needs. This
multi-faceted approach mitigates threats more effectively and ensures the
protection of valuable digital assets. A single security layer, when deployed
independently, is inherently weaker than multiple layers working in concert.
By employing a variety of security measures,
organizations can construct a comprehensive safety net that addresses diverse
attack vectors. This all-encompassing strategy minimizes the risk of single
points of failure and reduces the probability of unauthorized access. If one
security layer becomes compromised, the remaining layers continue to function
effectively, thwarting further infiltration.
As cyber threats persistently evolve in
complexity and sophistication, adopting a layered defense strategy is crucial
for organizations to remain proactive and responsive. This approach not only
strengthens the overall security posture but also safeguards sensitive data and
systems from potential breaches.
With that in mind, let's compare some
firewalls and examine the facts. We will look at several different product
dashboards, and provide brief capabilities;
Palo Alto NG
Firewalls
Cisco
Firepower Threat Defense
Fortigate
Meraki MX
Firewall
Sonicwall
Ubiquiti
UniFi Geo IP Filtering
|
Firewall Solution
|
Geo-blocking Features
|
|
|
Palo Alto
|
- Geo-based policy enforcement
- Integration with Threat Intel feeds for IP reputation
- Blocking traffic based on Src or Dst country
- Layer 7 User and Application
|
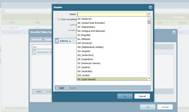
|
|
Cisco Firepower Threat Defense
|
- Geo-location-based access control
- Integration with Cisco Talos Intel Group for IP reputation
- Customizable filtering based on country or region
|
|
|
Fortigate
|
- Geo-IP address filtering
- Integration with FortiGuard Threat Intel for IP reputation
- Customizable filtering based on country or region
|
|
|
Meraki MX Firewall
|
- Geo-IP based firewall rules
- Blocking or allowing traffic based on src or dst country
- Built-in Layer 7 application-based filtering
|
|
|
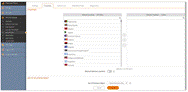
SonicWall
|
- Geo-IP based filtering
- Integration with SonicWall Capture Labs for IP reputation
- Customizable policies based on Src or Dst country
|
|
|
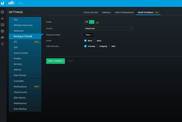
Ubiquiti UniFi
|
- Basic geo-blocking functionality
- Customizable filtering based on src or dst country
- Limited integration with external threat intel feeds
|
|
Notes from Field - Lets be honest you will
notice some of these firewalls have a capability of configuring Applications,
and Users geographically. Not only would
this become overwhelmingly complex, given the intricacies involved. The
likelihood of causing productivity disruptions is high. For instance, would
painstakingly need to understand their application environment to granular
details just to begin configuring these settings. The likely result is in a
very limited or broad control use of applications and user controls based
countries.
Imagine you want to allow FTP access in China.
You could effortlessly create a policy that permits TCP/21 in China. Suppose
you'd like to go further and block traffic to and from China and the
Netherlands. This, too, can be achieved relatively easily.
At first glance, the configuration appears to
be a solid strategy. Traffic to and from China and the Netherlands will be
blocked while allowing FTP access to China. However, let's take a closer look
at the potential consequences:
The FTP rule
grants FTP access to the entire country of China. Although you can refine
the rule by adding permitted users or specific destinations, managing and
curating this list against other lists or groups can quickly become
overwhelming.
The China
and Netherlands block has more significant repercussions. Soon after
enabling this rule, you may notice spotty services and users complaining
about inconsistent application reliability. The primary cause is the
reliance of these applications on cloud services or other unknown
connections to businesses within these countries. While administrators may
try to address this with additional policies, they will likely find the
task time-consuming and nearly impossible due to the variety of networks involved.
In short order, these rules may be disabled.
The root of this problem lies in need for more
visibility within the countries. China and the Netherlands are major hubs for
services like Microsoft, Azure, AWS, Cloudflare, and Akamai, as well as
services like DNS, NTP, and others, which impact reliable connectivity. The
concept of "blocking a country" is not truly feasible, except for
specific countries like those under OFAC/ITAR regulations. So, what's your next
move? Your only realistic option is continually adding security policies and engaging
in a never-ending game of whack-a-mole. This approach is neither practical nor
feasible, as evidenced by personal experience. Consequently, this is where
granularity ends for many of these firewalls that offer geo-blocking.
You might consider using a proxy and enabling
categories to address the granularity issue. However, this comparison is like
apples and oranges, and believing it will solve the problem is misguided. The
complexity and potential additional licensing costs to implement these services
can be challenging. Still, it doesn't resolve the issue, as proxy categories
and country blocking are two distinct concepts.
A compelling argument as to why proxy
categories and country blocking are different revolves around their distinct
objectives, methods of implementation, and scope.
Objectives:
Proxy categories filter content based on predefined categories, such as
social media, adult content, or gaming sites. This approach aims to
restrict access to specific types of content, ensuring compliance with
company policies or legal regulations. On the other hand, country blocking
is concerned with limiting or permitting network traffic based on the
geographic location of the source or destination IP addresses. This method
is typically used to mitigate threats from specific countries or comply
with international trade restrictions.
Methods of
Implementation: Proxy categories rely on URL filtering, which involves
comparing requested URLs against a database of categorized websites. When
a user tries to access a site, the proxy checks the site's category and
either allows or denies access accordingly. In contrast, country blocking
operates at the IP level, analyzing the source or destination IP addresses
of incoming or outgoing network traffic. The traffic is denied if the IP
address belongs to a blocked country.
Scope: Proxy
categories focus on web traffic content, allowing for more granular
control over the specific types of websites and web services that users
can access. This approach better addresses content filtering,
productivity, or compliance issues. Country blocking, however, is a
broader measure that affects all traffic originating from or destined for
a particular country without considering the content or purpose of the
traffic. This method is more suitable for addressing security concerns,
such as nation-state cyber threats or compliance with international
regulations.
You may also believe that the included
Intrusion Detection System (IDS) or Intrusion Prevention System (IPS) can
compensate for any vulnerabilities created by permitting or denying access
based on country. Nevertheless, it's important to remember that IDS and IPS
rely on known intelligence. Expanding on the argument that Intrusion Detection
Systems (IDS) and Intrusion Prevention Systems (IPS) are not adequate
substitutes for country blocking in cybersecurity, consider the following
points:
Reactive vs.
Proactive Measures: IDS and IPS are primarily reactive, relying on known
signatures, behaviors, or anomalies to detect and potentially block
attacks. They are effective at mitigating known threats but may be less
effective against emerging or unknown threats. On the other hand, Granular
Country Targeting is a proactive measure that seeks to prevent potential
threats originating from specific geographic locations and further within
the country before the event begins, even if the threats themselves are
not yet identified.
Limited
Visibility: IDS and IPS monitor and analyze network traffic for suspicious
activities or patterns. While they provide insight into ongoing attacks or
malicious activities, they cannot offer the same preemptive geographic
visibility as granular country targeting. Consequently, they may need to
be more effective in addressing threats specifically tied to certain
interior locations of a country or an organization. For example, in the
LOG4J attack, where companies such as Tenable, Oracle, Hetzner, and hundreds
of other businesses were located in dozen of countries, basic country
blocking nor IDS/IPS was effective.
Scope of
Protection: Although IDS and IPS can detect and mitigate various types of
attacks, such as malware, DDoS, and zero-day exploits, they cannot address
all aspects of cybersecurity that country-specific considerations may
impact. For instance, they cannot directly enforce compliance with
international trade restrictions, data residency laws, or other
location-based regulatory requirements.
Granularity:
IDS and IPS primarily function at the network layer, examining packets and
traffic patterns. In contrast, granular country targeting operates at the
IP layer, which through a protected process, associates IP to countries
and, in the best case, businesses that provide more granular control over
the source and destination of network traffic. This difference makes
granular country targeting more suitable for addressing location-based
threats and regulatory requirements.
Complementary
Technologies: IDS and IPS are essential components of a robust
cybersecurity strategy, but they should not be considered stop-gap for
granular country targeting. Instead, they should be used with other
security measures, including country blocking and, best scenario, granular
country targeting, to create a comprehensive defense against cyber
threats.
PacketViper Granular
Geo-Targeting.
Upon logging into the PacketViper platform,
users are instantly greeted with visually engaging and context-rich dashboards.
These dashboards deliver accurate and succinct telemetry data concerning the
sources and destinations of network traffic. The information is presented in
various formats, including source and destination countries, business networks,
protocols, and network ports. Users will also find convenient controls to
personalize their dashboard and configure individual widgets to suit their preferences.
A diverse array of widgets can be added to the
dashboard, allowing for a tailored experience tailored to each user's needs.
Configurable widgets enable users to target and display specific elements such
as segments, services, countries, business networks, network protocols, and
ports. Dashboards can be easily imported and exported between PacketViper
instances and shared among users within the same unit, promoting seamless
collaboration and customization.
For example, in the screenshot below, we have
selected the Geo dashboard, broken out into geographical regions, and a summary
widget for top countries.
In the image below, observe the context-rich
data featuring flag icons representing the countries within the connection
stream. These clickable flag icons offer a more focused view based on the
selected country. The solution delivers granular, geo-targeted telemetry that
accurately reflects activities from distinct regions, countries, and
businesses. It incorporates user-friendly techniques to delve deeper into the
network traffic, ensuring enhanced visibility and control for a comprehensive
understanding of the data.
Once the user selects the flag icon, another
window will launch and display the activity of that country exclusively. From
these windows, they can select IP addresses and business names from this
country or simply filter the country.
The user can simply click the Filtering tab
and select the direction and the ports to all or block.
If the user chooses to select an IP address, a
NetCheck screen will appear. This screen
will display comprehensive details about the IP and offers various tools for
further analysis. NetCheck grants users an in-depth view of the selected IP
address, allowing them to assess and make informed decisions.
For instance, users can create policies for
the IP, manage network assignments, examine the associated business, or explore
the country's data—all from a single, unified interface. This streamlined
approach ensures complete visibility and control over the IP and its
connections.
Should the user investigate the business for a
more comprehensive understanding, they can simply select the business name and
analyze its activity. This allows users the flexibility to apply filters at the
port level to a specific business, enabling them to mitigate risks originating
from the business-assigned network proactively, the single IP address, or the
broader approach of blocking the country. This selective targeting approach
empowers users to make well-informed decisions while maintaining a broader
perspective on potential threats. In this detailed view, the user will be
presented with the original country and all the countries this business may be
used against your network.
As illustrated in this screenshot below, the
Business Intelligence screen provides comprehensive insights into the business,
including its purpose and any pertinent recommendations, enabling users to make
well-informed decisions.
Users can refine their filtering preferences
for this business within the Filter tab. Users can precisely manage the network
connections and ports associated with the business by specifying the network
port to allow or block, ensuring only authorized access is permitted.
Users have the option to apply business
filtering based on the business name with ease. Users can effectively manage
their filtering preferences by accessing the Global Network Lists, entering the
desired business name, and customizing the filtering options.
The Business Intelligence lists offer a
tailored approach, allowing users to select a specific business and the country
in which it operates. By simply entering the business name and making the
appropriate selections, users can access targeted information for their needs.
Exploring Additional Applications
of Geo-Targeting
As you can see, the dashboard, which is tied
to granular geo-targeting, provides a simple mechanism to understand and
control the connection flow throughout the environment. Now that we have provided the advantage of
how information is received and network connections controlled
geographically. We are now going to
overlay another capability that uses geo-targeting.
Moving target defense (MTD) is an advanced
cybersecurity approach that dynamically changes the attack surface to confuse
and deter adversaries. By leveraging granular geo-targeting, MTD enhances its
effectiveness and adds an additional layer of complexity for attackers. This
innovative method allows for the customization of decoy responses according to
specific parameters such as country, business network, network port, connection
rate, and time of day. This dynamic alteration of decoy responses confounds cybercriminals
by forcing them to deal with a constantly changing environment, making it
increasingly challenging to succeed in their malicious endeavors.
When integrated with moving target defense,
granular geo-targeting provides a potent combination that significantly
bolsters an organization's security posture. The ability to tailor decoy
responses based on an attacker's geographical location and other factors
considerably hampers their attempts to infiltrate a network or system. As a
result, this approach disrupts the attacker's reconnaissance process,
complicating their efforts to establish a foothold within the targeted
environment.
Furthermore, MTD's increased unpredictability
and adaptability with granular geo-targeting ensures that cyber defenses remain
proactive, resilient, and better prepared to withstand the ever-evolving
landscape of cyber threats.
Moving target defense (MTD) is not merely
about relocating assets to reduce the attack surface; instead, it adopts a more
strategic approach by incorporating decoy responses to saturate the attack
surface, effectively shrinking the overall target profile. This method
introduces an array of decoys and traps designed to confuse and mislead
adversaries, thereby increasing the number of false targets they must navigate,
significantly hindering their progress in launching a successful attack.
By inundating the attack surface with decoys,
MTD creates a smokescreen that obfuscates the genuine assets and services
within the system. This heightened uncertainty and unpredictability forces
attackers to expend additional time and resources as they must sift through the
myriad of false targets in search of genuine vulnerabilities.
Consequently, this strategy not only buys
valuable time for organizations to detect and respond to potential threats but
also raises the bar for cybercriminals, making it increasingly challenging for
them to compromise the actual target.
In essence, MTD with decoy responses
strengthens the security posture by transforming the attack surface into a
dynamic, ever-shifting landscape that keeps adversaries constantly guessing and
struggling to gain a foothold.
Geo-Targeted Moving Target Defense (MTD) process.
In the illustration below, you'll observe a
table representing our decoy orchestrator. Notice that each decoy response is
configured to vary based on specific time frames. For instance, between 1:00 pm
and 1:15 pm, the responder emulates an FTP, while at 1:15 pm, it transitions to
a Proxy response. However, the responses during these two time frames will
differ depending on the chosen country or business network to which the
responses are projected.
Decoy
Orchestration
|
Decoy
Response
|
IP
|
Decoy
Response Port
|
Response
|
Service
Mimic
|
Source
|
Time/
Scheduler
|
Rate
|
|
1
|
1.1.1.1
|
TCP/21
|
Welcome to NSA FTP
|
FTP
|
China, Russia
Comcast
|
1:00 pm - 1:15 pm
|
1 in 30-sec
|
|
1
|
1.1.1.1
|
TCP/8080
|
Welcome to Proxy server
|
Proxy
|
Italy, UK, Canada, Russia
Akamai
|
1:15 pm - 1:30 pm
|
1 in 30-sec
|
|
2
|
1.1.1.2
|
TCP/21
|
Welcome to Pottery Barn
|
FTP
|
China, Russia
Iran
Belgium
|
1:00 pm - 1:15 pm
|
1 in 30-sec
|
|
2
|
1.1.1.2
|
TCP/3389
|
RDP Response
|
RDP
|
China, Russia
Australia
Cloudflare
|
1:15 pm - 1:30 pm
|
1 in 30-sec
|
|
2
|
1.1.1.2
|
TCP/25
|
Welcome to Pottery Barn SMTP
|
SMTP
|
China, Russia
Cloudflare
|
1:30 pm - 1:45 pm
|
1 in 30-sec
|
|
3
|
1.1.1.3
|
TCP/21
|
Welcome to the White House
|
FTP
|
China, Russia
Australia
|
1:00 pm - 1:15 pm
|
1 in 30-sec
|
|
3
|
1.1.1.3
|
TCP/22
|
Welcome to the White House
|
SSH
|
China, Russia
Canada
|
1:15 pm - 1:30 pm
|
1 in 30-sec
|
You might be concerned that managing such a
system could become unwieldy; however, we have already taken this into account
by incorporating user-friendly drop-down options and selectable groups.
Orchestrating our MTD strategy requires just a few clicks, streamlining the
process for users. The key takeaway is that a simple country-blocking approach
alone is insufficient to achieve this level of granularity for a Moving Target
Defense. Instead, geo-targeting incorporated MTD creates a formidable, if not impossible,
defense strategy to overcome given the obfuscation of the network boundary.
Overcoming Geo-Blocking: The
Power of Proxy Connections.
A proxy server can be used to bypass
geo-blocking by acting as an intermediary between the user's device and the
target website or service. When a user connects to a proxy server located in a
different country, their internet traffic is routed through that server before
reaching the target destination. This process effectively masks the user's
actual IP address and replaces it with the proxy server's IP address.
Since geo-blocking typically relies on the
user's IP address to determine their geographical location, utilizing a proxy
server in a different country can deceive the target website or service into
believing that the user is accessing it from an allowed region. Consequently,
the user can circumvent geo-blocking restrictions and access the desired
content or services, even if they are located in a region where access is
normally restricted.
The primary reason for this is that
geo-blocking generally isn’t applied to the country the user is operating from,
or countries they may do business with.
So naturally the user leaves many countries open and attempts to shut
down the usual suspects. A here lies the problem, the attackers know this and
therefore use proxy connection to circumvent these geo-blockers. For example an attacker desires to scan a US
company. The attacker proxies into the
US and scans its target. Its pretty straight forward.
Closing
the Proxy Loophole with PacketViper’s Granular Geo-Targeting
When tested through PacketViper’s granular geo-targeting,
the traditional proxy bypass tactic immediately fails. PacketViper not only
recognizes the apparent U.S. connection but also correlates the *business
network* behind the proxy. Instead of accepting the traffic based solely on the
IP’s country assignment, PacketViper evaluates the *network owner*, *autonomous
system number (ASN)*, *business identity*, and *behavioral reputation.*
This level of visibility ensures that malicious activity hosted within trusted
geographic zones is still detected, flagged, and automatically mitigated —
without blocking legitimate users in the same region.
Whereas conventional firewalls see a connection as simply “traffic from the
United States,” PacketViper distinguishes whether that traffic originates from
a cloud provider, anonymizing proxy, or legitimate U.S. enterprise. By
maintaining continuous correlation with business-level intelligence,
PacketViper prevents adversaries from hiding behind global infrastructure-as-a-service
providers like AWS or Azure.
Applied
Intelligence and Automated Enforcement
PacketViper’s **Applied Intelligence** transforms geo and behavioral data into
immediately enforceable defense actions. When a threat is detected:
· The detecting PacketViper
automatically generates a local blacklist rule and blocks the source.
· The rule is propagated through the
Central Management Unit (CMU) to all connected PacketVipers.
· No rerouting occurs — the traffic
is simply stopped at the edge.
This rapid, autonomous response eliminates the need for manual intervention and
prevents lateral movement across the enterprise. As a result, organizations
benefit from near real-time defense enforcement that extends beyond static IP
reputation lists and threat feeds.
Preventive
Cyber Defense Through Deception and Visibility
When combined with PacketViper’s **Active Deception** capabilities, such as
Deceptive Responders and DR ID Decoys, granular geo-targeting becomes even more
potent. These responders generate misleading yet believable data that confounds
reconnaissance attempts, captures credentials, and instantly blocks the
attacker.
Even if a malicious actor attempts to pivot through a proxy network,
PacketViper’s contextual awareness exposes the deception, identifies the
business entity hosting the proxy, and enforces an immediate block — all
without revealing its presence. This stealth enforcement is critical for
maintaining operational continuity in both IT and OT environments.
Business and
Operational Advantages
1. Reduced Complexity: Administrators
manage threats through a visual, context-driven interface that maps threats by
country, business, and network segment.
2. Performance Efficiency: By filtering at the edge and eliminating
unnecessary logging, PacketViper reduces SIEM load and extends the life of the
existing security stack.
3. Vendor and Regulatory Assurance: Geo-targeting at the business level
supports vendor risk management and compliance with trade and data residency
regulations.
4. Enhanced Situational Awareness: Real-time dashboards correlate threat
origin, destination, and intent — turning raw telemetry into applied
intelligence.
In a digital landscape where attackers exploit cloud platforms and proxy
infrastructures to conceal their origins, legacy country-blocking has lost its
effectiveness. PacketViper’s Granular Geo-Targeting replaces static,
one-dimensional filtering with a dynamic, context-aware defense framework.
By merging geography, business intelligence, and deception, PacketViper creates
a living perimeter - one that adapts, responds, and evolves faster than
adversaries can pivot. This capability not only closes the proxy loophole but
also establishes the foundation for Preventive Cyber Defense, ensuring
that every packet is evaluated within its true operational and business
context.
PacketViper transforms geo-blocking from a blunt instrument into a precision
defense weapon — redefining the boundaries of network security